Auth0
info
For SSO Access - please reach out to sales team.
This article briefs about the steps to configure Auth0 as Identity service provider for NocoDB
NocoDB, Retrieve Redirect URL
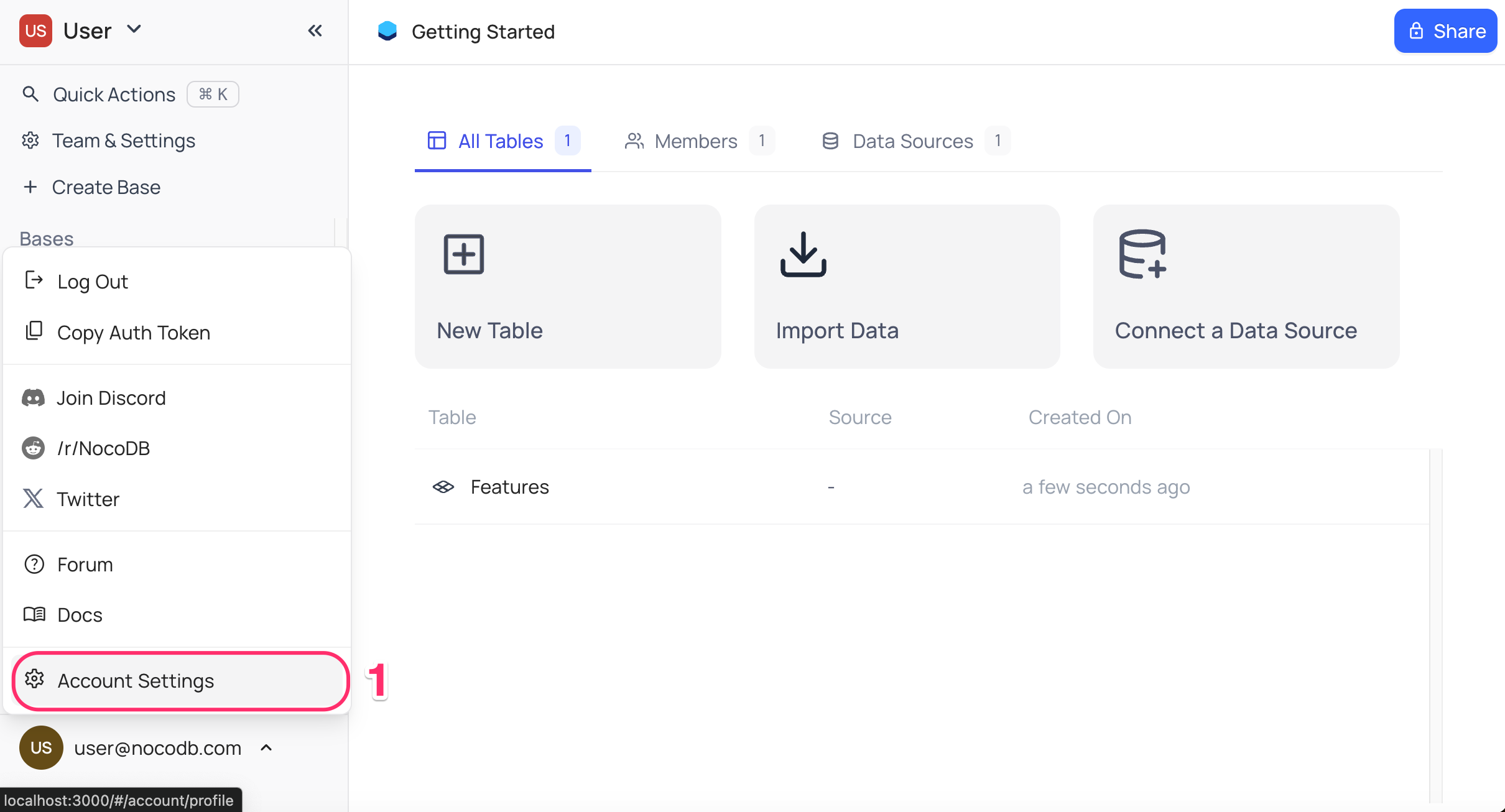
- Go to
Account Settings - Select
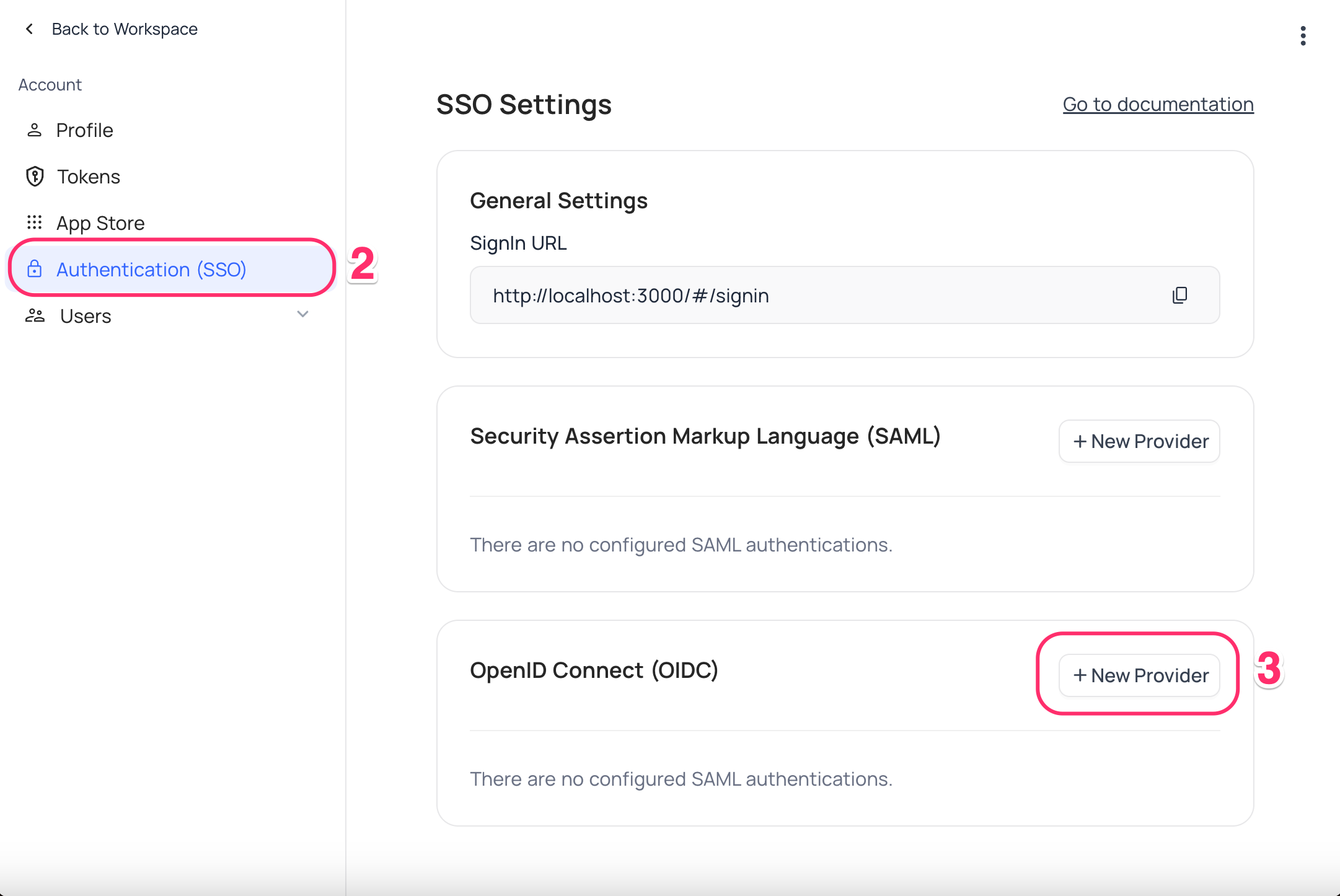
Authentication (SSO) - Click on
New Providerbutton - On the Popup modal, Specify a
Display namefor the provider; note that, this name will be used to display the provider on the login page - Retrieve
Redirect URL; this information will be required to be configured later with the Identity Provider
Auth0, Configure NocoDB as an Application
- Access your Auth0 account
- navigate to
Applications>Create Application.
- navigate to
- In the
Create Applicationmodal,- choose
Regular Web Application - click
Create
- choose
- On Quick start screen, go to
Settingstab- Copy the
Client IDandClient Secretfrom theBasic Informationsection.
- Copy the
- Goto
Application URIssection- Add the
Redirect URLcopied from step(2) underAllowed Callback URLs. Save Changes
- Add the
- On the
Settingstab, go to theAdvanced Settingssection and click on theEndpointstab.- Copy the
OAuth Authorization URL,OAuth Token URL,OAuth User Info URL&JSON Web Key Set URL
- Copy the
NocoDB, Configure Auth0 as an Identity Provider
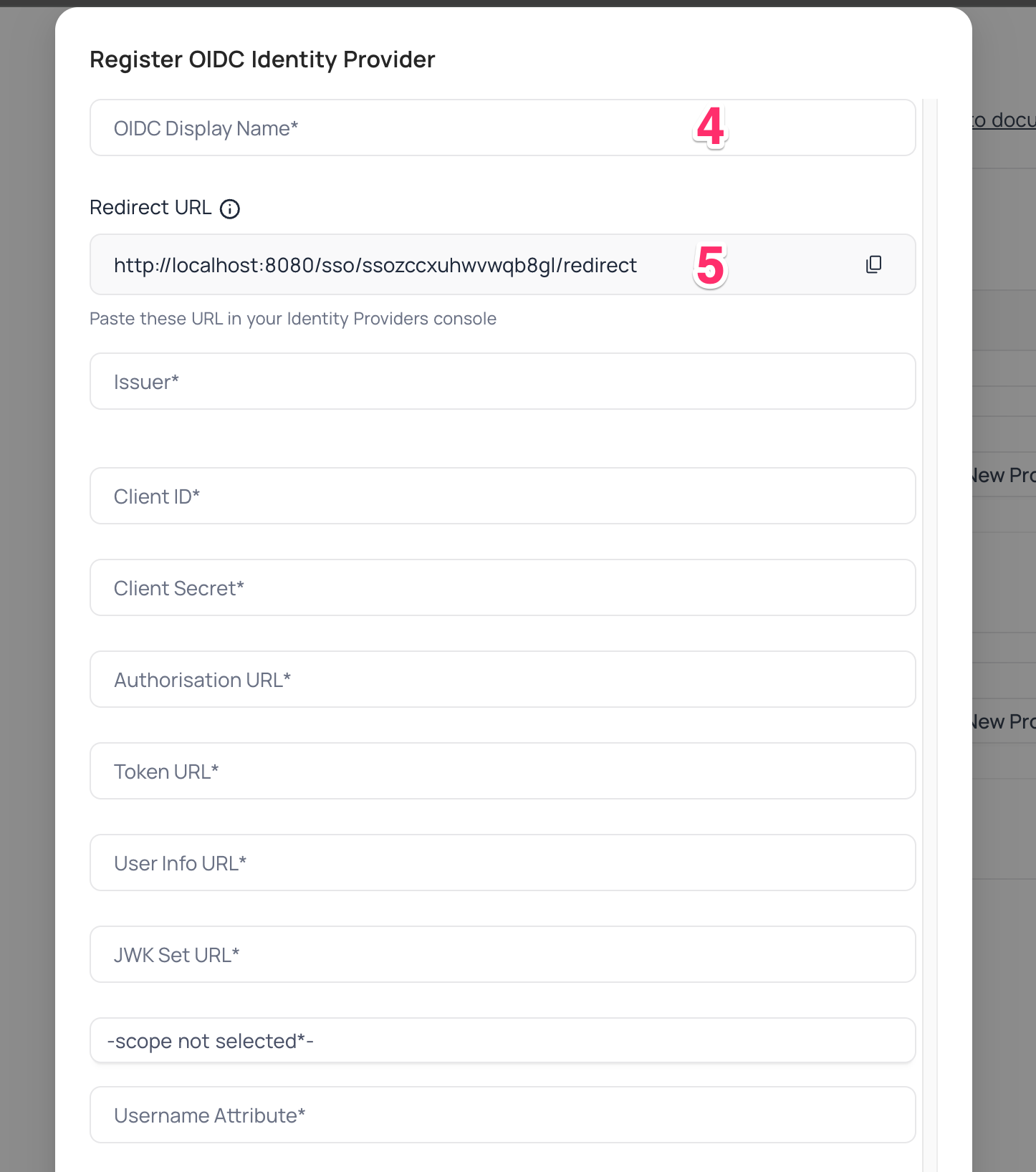
- In NocoDB, open
Account Settings>Authentication>OIDC. On the "Register OIDC Identity Provider" modal, insert the following information:- Insert
Client IDretrieved in step (5) above asClient ID - Insert
Client Secretretrieved in step (5) above asClient Secret - Insert
OAuth Authorization URLretrieved in step (7) above asAuthorization URL - Insert
OAuth Token URLretrieved in step (7) above asToken URL - Insert
OAuth User Info URLretrieved in step (7) above asUserinfo URL - Insert
JSON Web Key Set URLretrieved in step (7) above asJWK Set URL - Set
Scopeasopenidprofileemailoffline_access - In the Username Attribute field, indicate the name of the claim that represents the user's email. The default value is set to "email."
- Insert
For Sign-in's, user should be able to now see Sign in with <SSO> option.
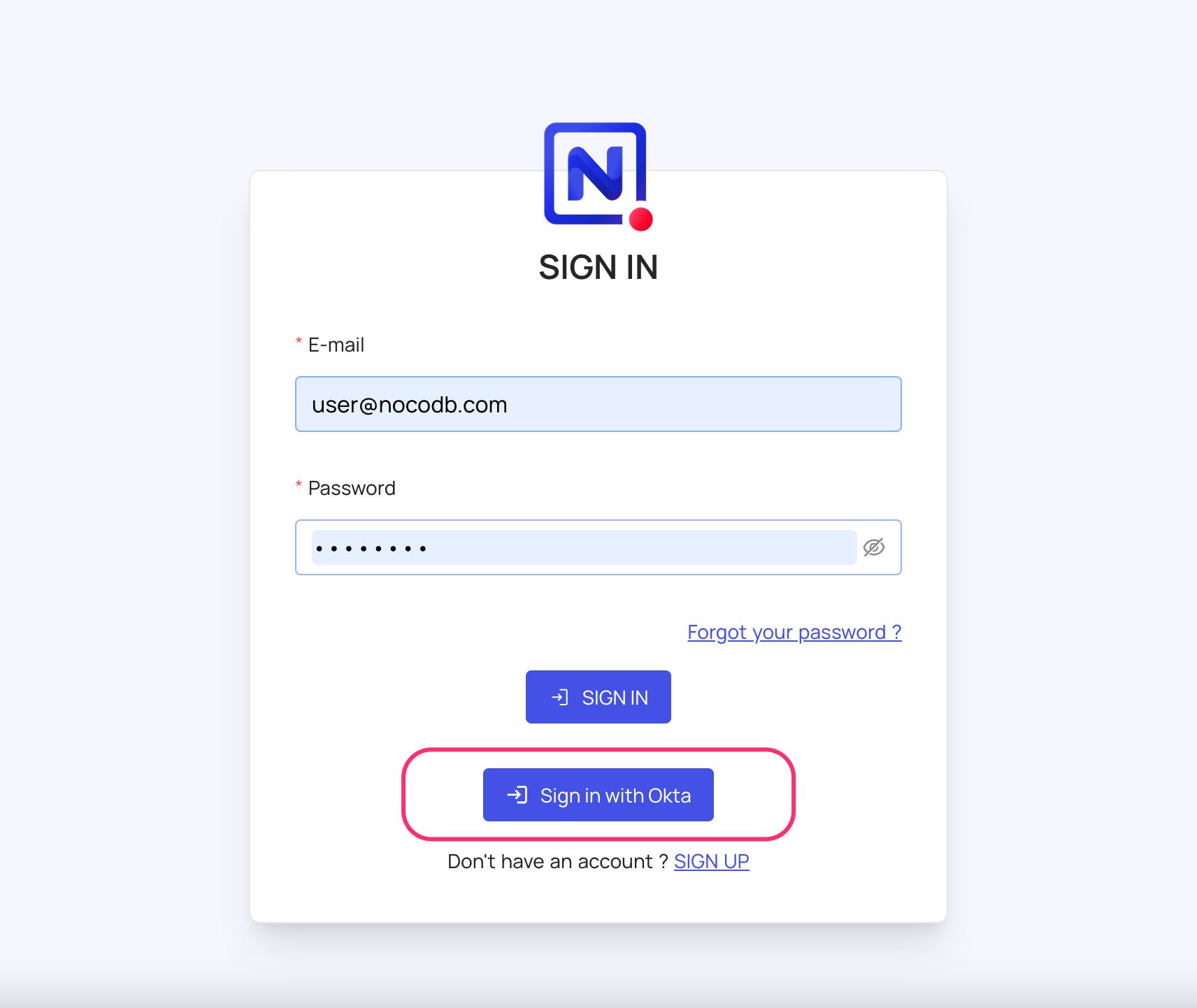
note
Post sign-out, refresh page (for the first time) if you do not see Sign in with <SSO> option
For information about Auth0 API Scopes, refer here