Okta
info
For SSO Access - please reach out to sales team.
This article briefs about the steps to configure Okta as Identity service provider for NocoDB
NocoDB, Retrieve SAML SSO Configuration details
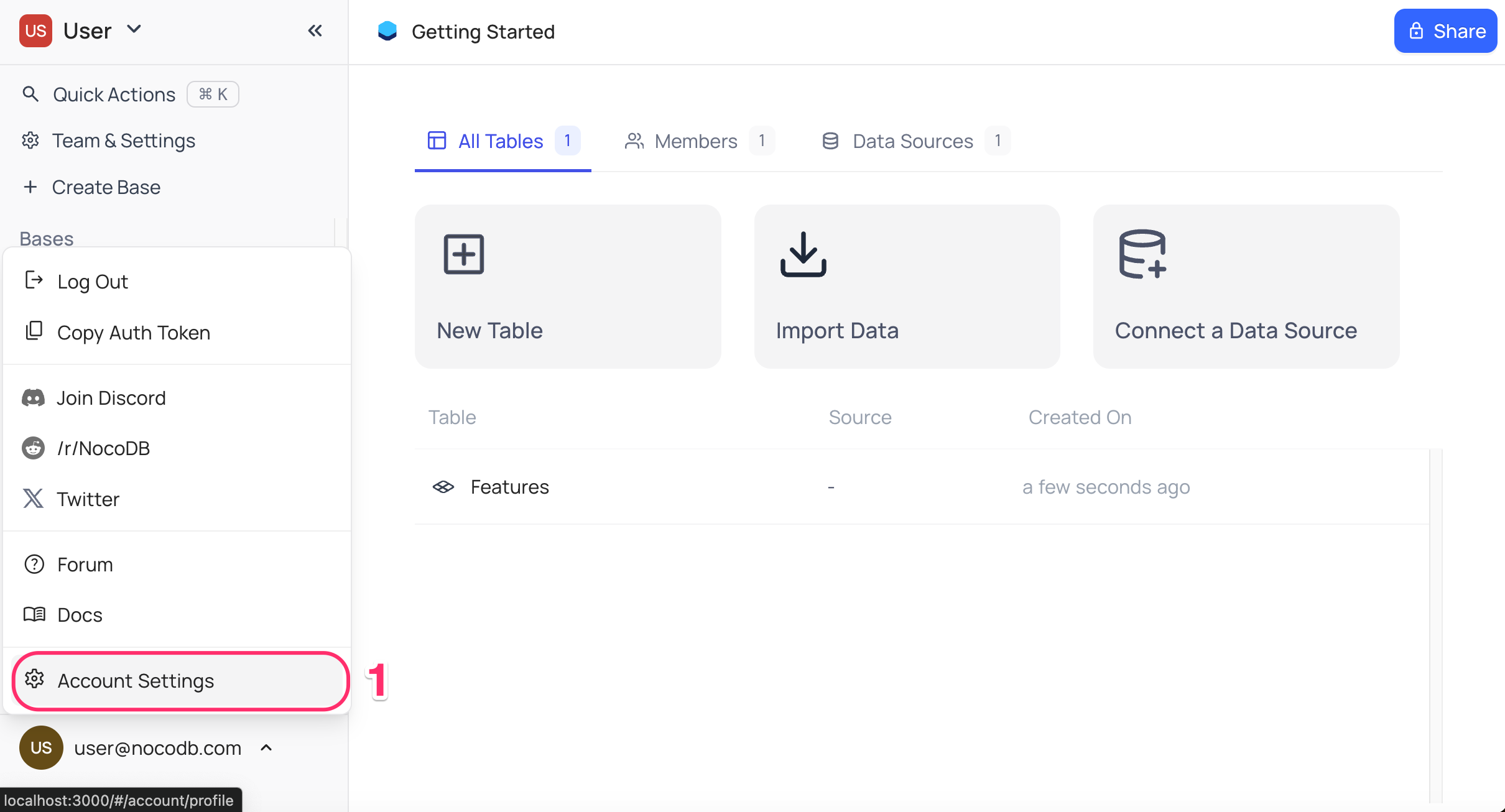
- Go to
Account Settings - Select
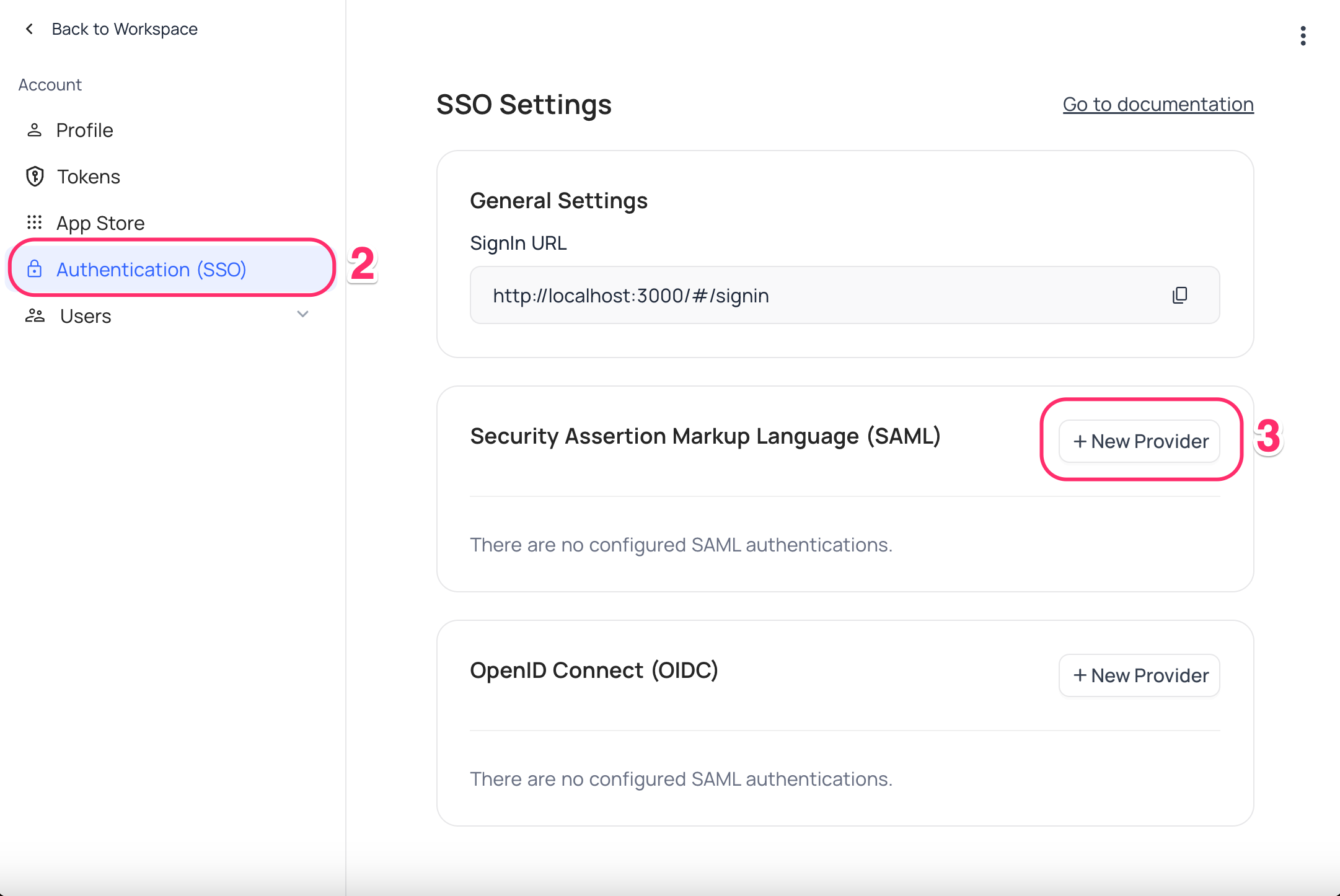
Authentication (SSO) - Click on
New Providerbutton - On the Popup modal, Specify a
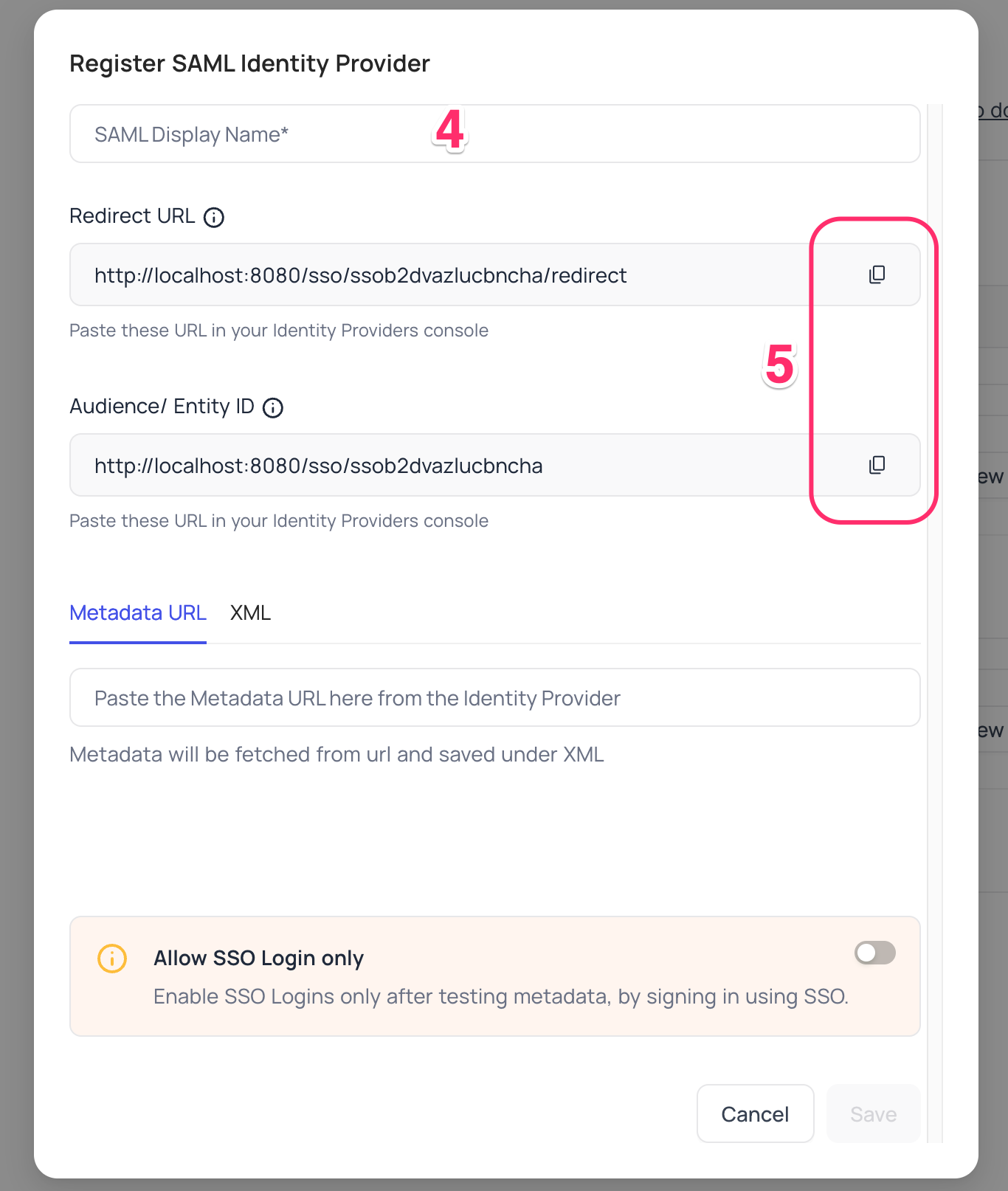
Display namefor the provider; note that, this name will be used to display the provider on the login page - Retrieve
Redirect URL&Audience / Entity ID; these information will be required to be configured later with the Identity Provider
Okta, Configure NocoDB as an Application
- Sign in to your Okta account
- Navigate to
Applications>Applications - Click
Create App Integration
- Navigate to
- In the pop-up with title
Create a new app integrationchooseSAML 2.0as the Sign-in method - On the
Create SAML Integrationpage, in the General settings - provide a name for your app; clickNext - In the
Configure SAMLsection:- Enter the
Redirect URLcopied from NocoDB in theSingle sign-on URLfield. - Add the
Audience URIcopied from NocoDB in theAudience URI (SP Entity ID)field. - Choose
Email Addressfrom theName ID formatoptions. - Select
Emailfrom theApplication user-nameoptions. - Click
Next
- Enter the
- Complete any additional information in the final step and click
Finish - On your application's homepage,
- Navigate to the
Sign-ontab - Copy the
Metadata URLfrom theSAML 2.0section
- Navigate to the
- Go to the
Assignmentstab and clickAssignto assign people or groups to this application.
NocoDB, Configure Okta as an Identity Provider
- Go to
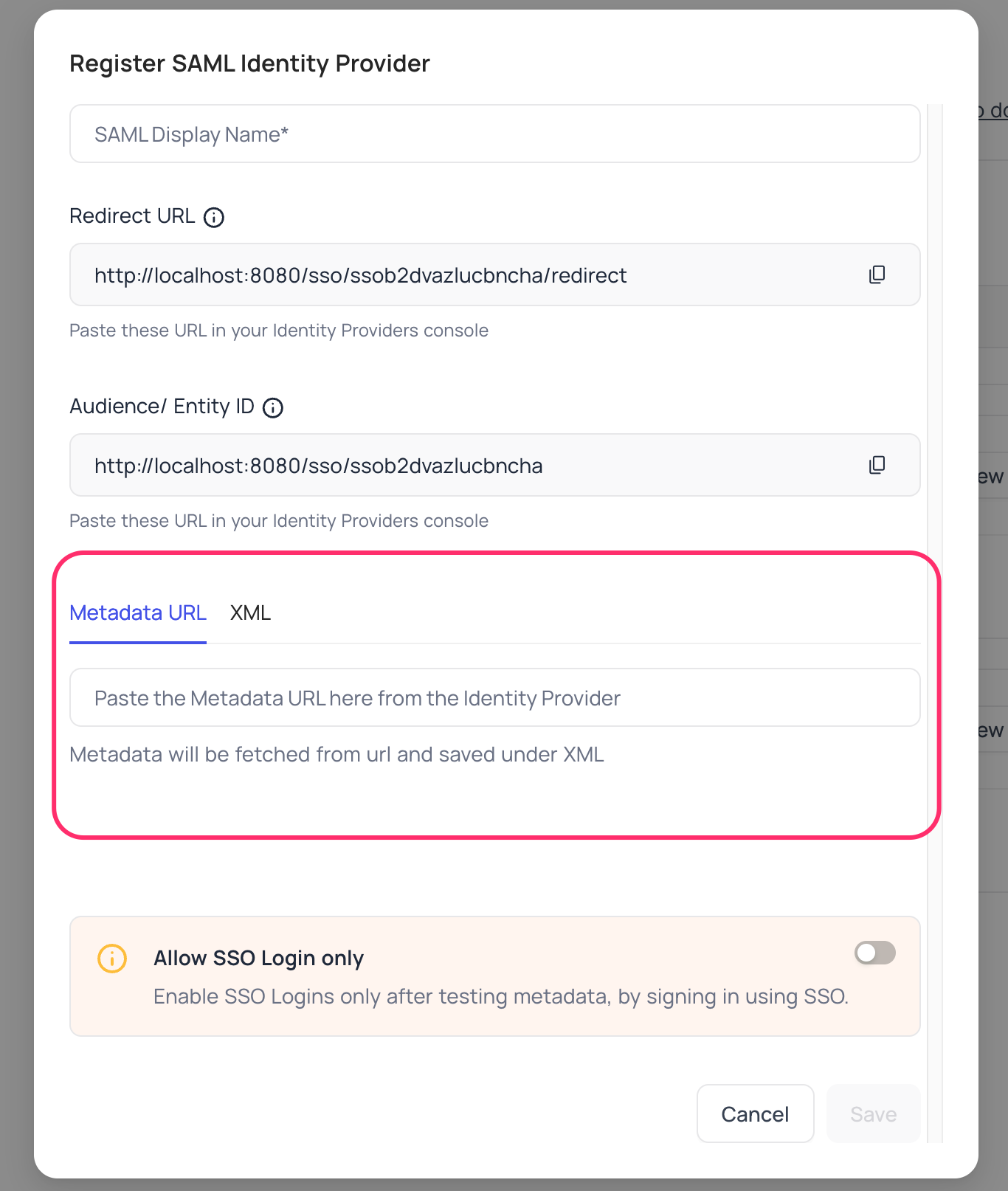
Account Settings>Authentication (SSO)>SAML - On the "Register SAML Identity Provider" modal, insert
Metadata URLretrieved in step above; alternatively you can configure XML directly as well Save
For Sign-in's, user should be able to now see Sign in with <SSO> option.
note
Post sign-out, refresh page (for the first time) if you do not see Sign in with <SSO> option